Table of Contents
Before diving into the specifics of protocol ports, it’s important to understand what SNMP is. SNMP is a set of protocols for managing complex networks. It works by sending messages, called protocol data units (PDUs), to different parts of a network. Network administrators can use SNMP to monitor the health and performance of network devices, troubleshoot problems, and more.
The Role of SNMP Protocol Ports
SNMP operates over the Internet Protocol (IP) and uses specific ports to ensure the secure and reliable transmission of data. Ports, in the context of computer networking, are endpoint locations on a network device used by protocols to sort traffic and ensure it gets to the right application. For SNMP, there are two main ports involved:
Standard SNMP Ports
- UDP Port 161 – This is the default port used by SNMP for sending and receiving requests. When a network management system (NMS) wants to gather information from a network device, it sends a request to UDP port 161 on the device.
- UDP Port 162 – This port is used for SNMP traps. Traps are unsolicited notifications from an SNMP agent to the NMS, alerting it to a significant event or change in the network. By listening on UDP port 162, the NMS can receive these alerts and act accordingly.
Importance of SNMP Protocol Ports
Understanding and correctly configuring SNMP ports is crucial for effective network management for several reasons:
- Security: By knowing which ports SNMP uses, administrators can configure firewalls and other security measures to protect SNMP traffic from unauthorized access.
- Efficiency: Correct port configuration ensures that SNMP requests and traps are routed correctly, improving the responsiveness and reliability of network management.
- Troubleshooting: Identifying issues with SNMP communication often involves verifying that the correct ports are open and accessible on network devices.
Configuring SNMP Protocol Ports
Configuring SNMP ports typically involves setting up network devices and management systems to use the standard ports (161 and 162). However, for added security, administrators may choose to change these default port numbers. This requires configuring both the SNMP agents on the network devices and the NMS to use the new port numbers.
Best Practices for Managing SNMP Protocol Ports
- Monitor Port Usage: Regularly monitor SNMP port activity to detect unauthorized access attempts or misconfigurations.
- Use Firewalls: Configure firewalls to allow SNMP traffic only from trusted IP addresses.
- Change Default Ports: Consider changing the default SNMP port numbers to reduce the risk of attacks targeting these well-known ports.
- Keep Software Updated: Ensure that your SNMP software is up to date to benefit from the latest security patches and features.
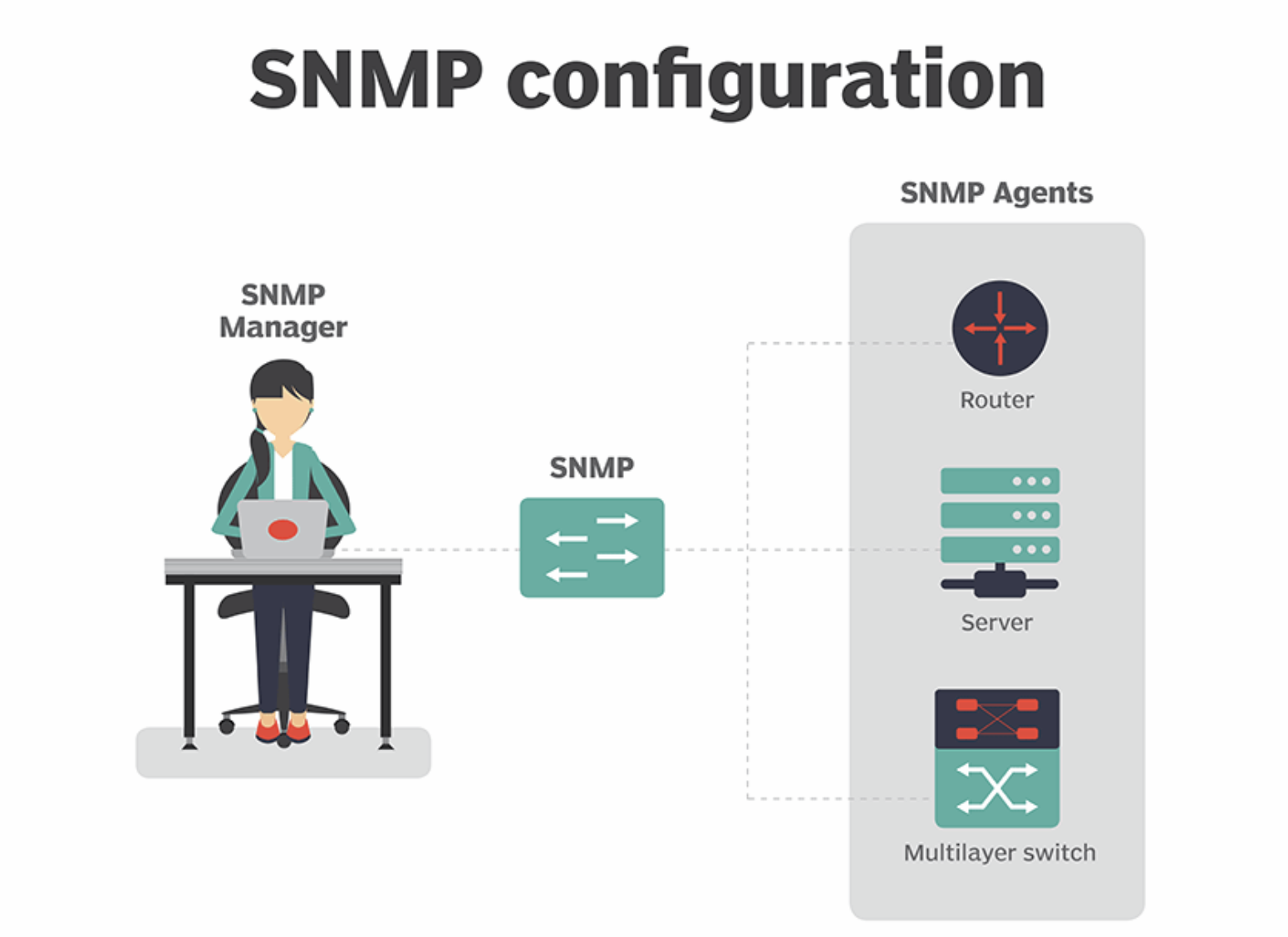
Key Components of SNMP
Understanding SNMP requires familiarity with its three primary components:
- SNMP Manager: This is the central system used to control and monitor a network of devices using SNMP. The manager sends requests to agents and receives responses and unsolicited traps from them.
- SNMP Agent: Installed on the network device, the agent acts as an intermediary between the device and the SNMP manager. It collects the management information database from the device and makes it available to the SNMP manager, responding to requests and sending alerts or traps.
- Management Information Base (MIB): The MIB is a collection of information organized hierarchically. It defines the data items a device can return, such as device status or network performance metrics. Each item is identified by an object identifier (OID).
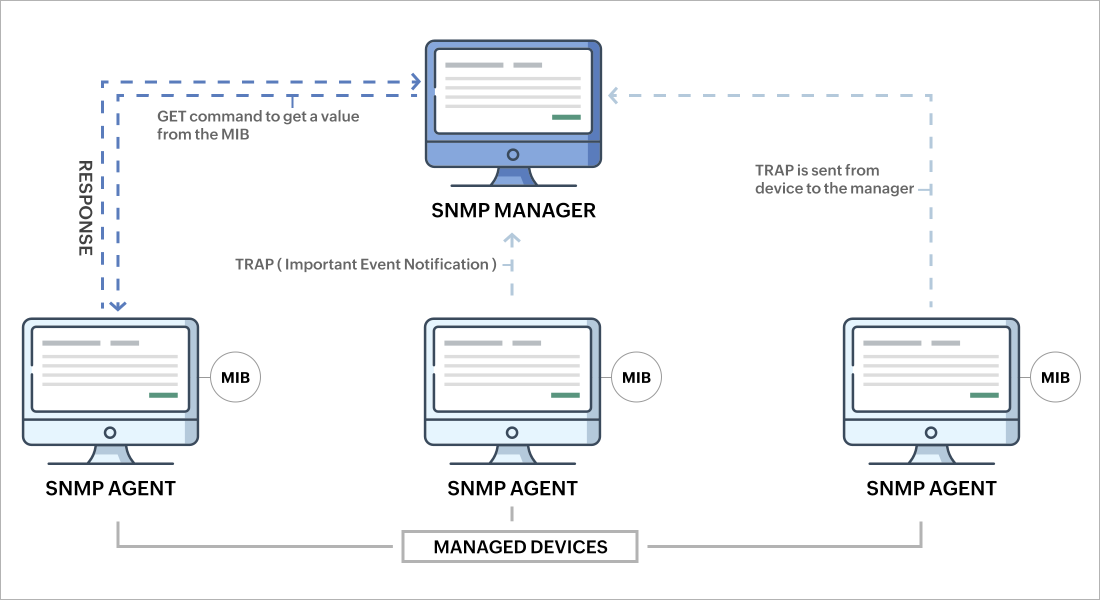
How SNMP Works
SNMP operates based on a simple request-response model. Here’s how the process typically unfolds:
- Request: The SNMP manager sends a request to an SNMP agent. This request can be for information retrieval (GET), configuration changes (SET), or other functions.
- Response: The SNMP agent processes the manager’s request, retrieves the necessary information from the device’s MIB, and sends back a response.
- Traps: Apart from the request-response mechanism, SNMP agents can also send unsolicited trap messages to the SNMP manager. Traps are notifications of significant events or changes in the network, such as a device going offline or a security breach.
SNMP Operations
SNMP defines several operations for communication between the manager and agents. The most commonly used are:
- GET: Retrieves the value of one or more specific items from an agent’s MIB.
- SET: Modifies or assigns the value of one or more items in an agent’s MIB.
- GETNEXT: Requests the next data item in an agent’s MIB, facilitating browsing of the MIB.
- GETBULK: Allows the retrieval of large volumes of data from an agent’s MIB in a single request.
- TRAP: Sent by an agent to the manager to indicate an event or change.
Versions of SNMP
There are three major versions of SNMP, each offering different features and levels of security:
- SNMPv1: The original version, which offers basic features and minimal security.
- SNMPv2c: Introduces improvements in performance, including the GETBULK operation, but still has limited security features.
- SNMPv3: Provides significant enhancements in security, including authentication and encryption of packets.
SNMP in Network Management
SNMP is crucial for effective network management for several reasons:
- Scalability: It can manage a small home network or scale to manage large enterprise networks.
- Flexibility: SNMP supports a wide range of devices and manufacturers.
- Efficiency: Automates the monitoring and management of network devices, reducing the need for manual intervention.
- Proactive Management: With traps, SNMP enables administrators to respond to issues immediately, often before users are affected.